In the modern age, a standout application development is the need of the hour. As every application is unique and focuses on providing top-quality services, yours needs to be just as efficient. Here is where Cloud-native architecture comes to play. The modular approach to app security in this methodology allows apps to develop into agile and dynamic applications that make all the difference around them.
But the question is, what is so different about the modular approach of this cloud technique that makes it break the traditional approach to app security? That is what we are here to uncover.
What Is Cloud-Native Architecture?
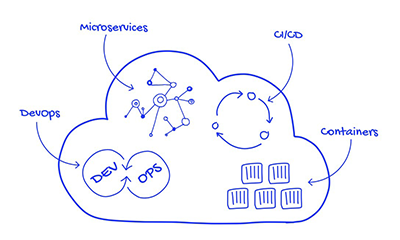
This methodology is what helps to build better scalability by implementing various cloud solutions and cloud computing. As a result, it helps develop efficiency, productivity, and effectiveness in no time. This allows the technique to formulate a tailored modular infrastructure. This design tool applies cutting-edge technology that enables companies to use their services by ensuring paramount app security. By using purpose-built tools and services, cloud app security helps make everything an effortless experience for you.
Read Also – Impact analysis of Covid-19 on Cloud Application Market
Cloud-Native Apps VS Traditional Approach
- Cloud-native apps are focused on a contract that is aimed at improving resilience via predictable conduct. But the traditional approach is often longer to create and doesn’t offer the benefits of a cloud-native app platform. Therefore, the latter showcases unpredictable behavior.
- Cloud-native apps allow the developers a technique to abstract away bordering infrastructure dependencies. Thus, it focuses on a formalized platform. But the traditional approach was OS-dependent. Therefore, these dependencies always made migrating and scaling the app a risky affair. It also becomes complex during the entire process. As a result, cloud-native app security proves to be a boon.
- Based on the application’s needs, the cloud-native app will automate its infrastructure deliverables and configure them at deploy time. So, it offers the right-sized capacity. But the traditional approach provided large capacity by delaying the deployment of the app. This only provided minimal ability to scale and satisfied worst-case capacity estimates.
- Cloud-native architecture is highly collaborative as it promises to smoothen the transfer of finished app code into production. On the other hand, the traditional approach is siloed, meaning it applies an over-the-top handoff of dead app code from developers to operations. So, the process is slow, inefficient, and provides compromised deliverables.
- Cloud-native apps provide continuous delivery to keep the flow of work uptight. On the other hand, the traditional approach offers a waterfall development that makes the brand miss many opportunities. As a result, the customers’ profitability observed a decreased growth rate. Also, it fails to offer customer satisfaction.
Read Also – The New Age: Cloud Computing in Agriculture Sectors
How Is Cloud-Native App Security Breaking The Traditional Approach?
Identity and Access

All cloud-native apps are supposed to provide access only to authenticated sources. This enables them to ensure that the app security remains intact. IBM Cloud ID stores all user data. This can be used in the application to support user engagement. The information may contain all about the user and their identity. Since sensitive microservices are available for global access, it is significant to create a user with certainty. This is more significant if the user base is full of customers, employees, contractors, and partners since they have umpteen access to confidential information.
Network Security

As much as customers want speed deliverables, compute-intensive servers, they also want to grasp efficient protection. Since insecure networks can be a hazard for the app security and provide denial-of-service attacks, it is essential to deal with them properly and ward off the risks. Cloud-native app security thus comes in handy here. Setting up a firewall that features custom network policies will help map out the risks and provide the proper remedy for network intrusion. Make sure you also open up the required ports and IP addresses for every location. This will enable the working nodes and the master to indulge in convenient communication. IBM Cloud Internet Services may offer to secure your internet apps against all types of cyber threats and attacks. So you can be at peace wherever you go.
Read Also – Tackling COVID-19: How Cloud Computing Throws a Lifeline to Businesses?
Application Isolation and Protection

Customers always demand app protection so that they can interact with risks at a minimum. This is what pushes companies to seek efficiency protection that lasts long-term. Customers also desire the complete separation and isolation of components in the app, memory, process, and network level. With the help of cloud computing companies, this problem is resolved in a minimal time frame. With container security, next-level automation can be expected that helps provide access control with authentication and renders utmost safety. Designated worker nodes as edge nodes to host Ingress Controller can help. Users can be authorized to segment the access management and deployment as well using network policy.
Data Security

Data is an essential asset to every business. Therefore, it is significant to preserve it and ensure that it promises utmost security to keep everything intact. With cloud computing companies, the solution for data security is not far away. IMB Key Protect offers roots of trust (RoT) backed by a hardware security module (HSM) So, the cloud-based security service promises lifecycle management for encryption keys. IBM Cloud Certificate Manager is also utilized to promote SSL certificates and associate private keys to provide security. It also helps with audit and governance certificate-related tasks that comply with the business’s policies.
Read Also – Prediction: 80% of Enterprise IT Will Move To the Cloud By 2025
Secure DevOps

The traditional approach to app security was outdated, effortful, and inefficient. But the modern-day method is far more convenient. By securing DevOps, one can make sure of the infrastructure and applications free from vulnerabilities and cyber attacks. Vulnerability Advisor allows you to conduct a live scanner. This will help scan security gaps effectively. IMB Application Security On Cloud secures your brand’s website and mobile apps by scanning them for vulnerabilities right on time. So, it does not allow any malicious activity to occur on the system.
The Bottom Line
Cloud-native architecture has proven to be a boon in the IT industry today. If you do not want to keep using the traditional approach to app security, it is best to switch to this timeless classic.